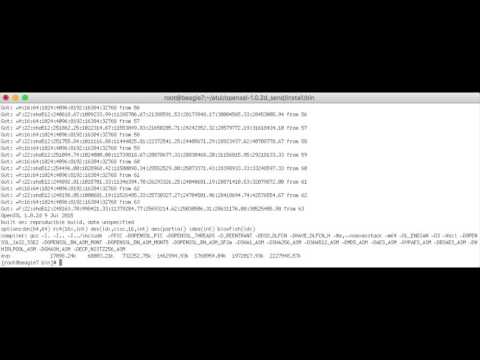
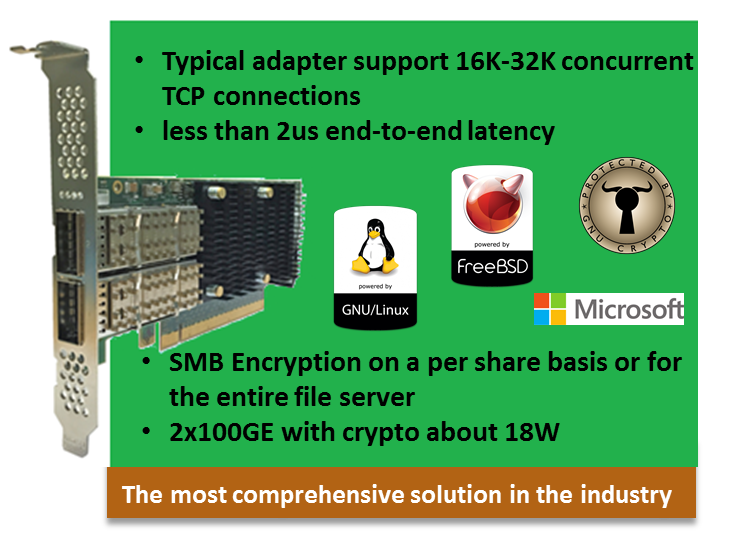
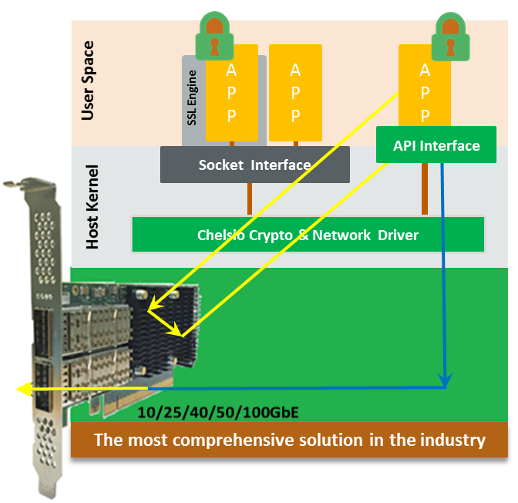
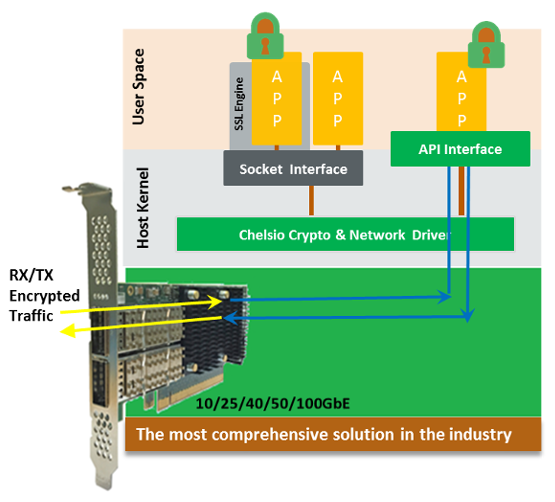
Chelsio’s Terminator 6 (T6) Unified Wire ASIC enables concurrent secure communication and secure storage with support for integrated TLS/SSL/DTLS and inline cryptographic functions, leveraging the proprietary TCP/IP offload engine for acceleration. Chelsio’s full offload TLS/SSL/DTLS is uniquely capable of 100Gb line-rate performance. DTLS runs on UDP, while TLS runs on TCP. In addition, the accelerator can be used in a traditional Co-processor Lookaside mode to accelerate TLS/SSL, IPsec, SMB 3.X crypto, data at rest encryption/decryption and data-deduplication fingerprint computations. With its sixth‐generation T6 ASIC and Ethernet adapters, Chelsio has taken the unified wire solution to the next level. T6 delivers an unmatched feature set combined with a single‐chip design. No other vendor offers a single SKU for NVMe-oF, NIC, TOE, SR-IOV, iSCSI, FCoE and iWARP RDMA that concurrently supports in-line TLS/SSL, SMB 3. X crypto, IPsec and DTLS. Key Features
Key Benefits
Supported Cryptographic Offload & Acceleration Modes
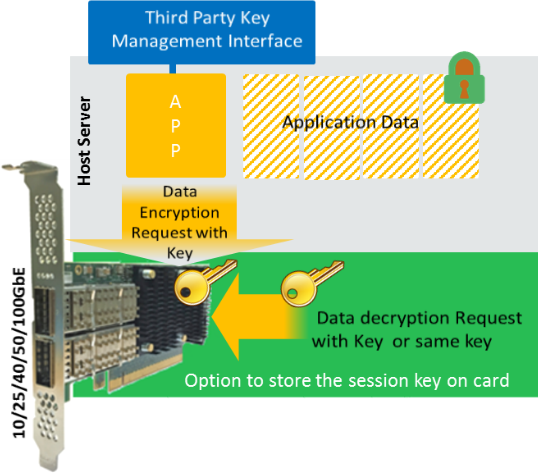
Cryptographic functions can be enabled in different mechanisms and support different protocols. At a high level, traditional Co-processor mode is known for processing data-at-rest encryption/decryption and data-deduplication fingerprint computation, while Inline Crypto mode has the capabilities to authenticate and process encrypted packets for the application at the port level and encrypt outgoing packets when requested by the application. Chelsio adapters support both modes and solution is programmable enough in nature to make the desired modifications for optimization. Traditional Co-processor Mode
This mode of operation is supported for TLS/SSL, SMB 3.X and IPsec protocols, for functionalities like data at rest encryption, decryption, authentication and data de-dupe fingerprint generation.
Inline Mode
Chelsio Inline crypto solution supports TCP/IP and TLS/SSL AES/SHA processing in cut-through fashion to achieve optimal bandwidth and latency. Offloaded connection is used to transmit and receive data. Handshake is executed in host while data is encrypted and decrypted by crypto engine offloaded to hardware.
Key Negotiation/Exchange
Chelsio cryptographic solution supports popular protocols like IKE (key negotiation), RSA, Diffie-Hellman, Elliptic Curver Cryptography (ECC), etc., provides encryption capabilities built into application with TLS/SSL and DTLS mechanisms. Chelsio adapters offload the TLS/SSL PDU crypto, while handshake and key exchange are still performed by the host. Key Negotiation Rate Use cases
Supported Operating SystemsCurrently Chelsio’s Crypto Offload drivers for Co-processor and Inline modes are available for Linux, supporting following kernel versions:
Linux drivers support both user-space as well as kernel-space module interfaces. The user-space applications can leverage the af_alg interface to use Chelsio crypto offload feature, while the kernel-space modules are supported directly using Linux’s crypto framework to access the Chelsio crypto offload features. Latest drivers/software are available at http://service.chelsio.com. Supported AdaptersThe following are the currently shipping Chelsio adapters that are supported and compatible with Chelsio’s crypto offload drivers:
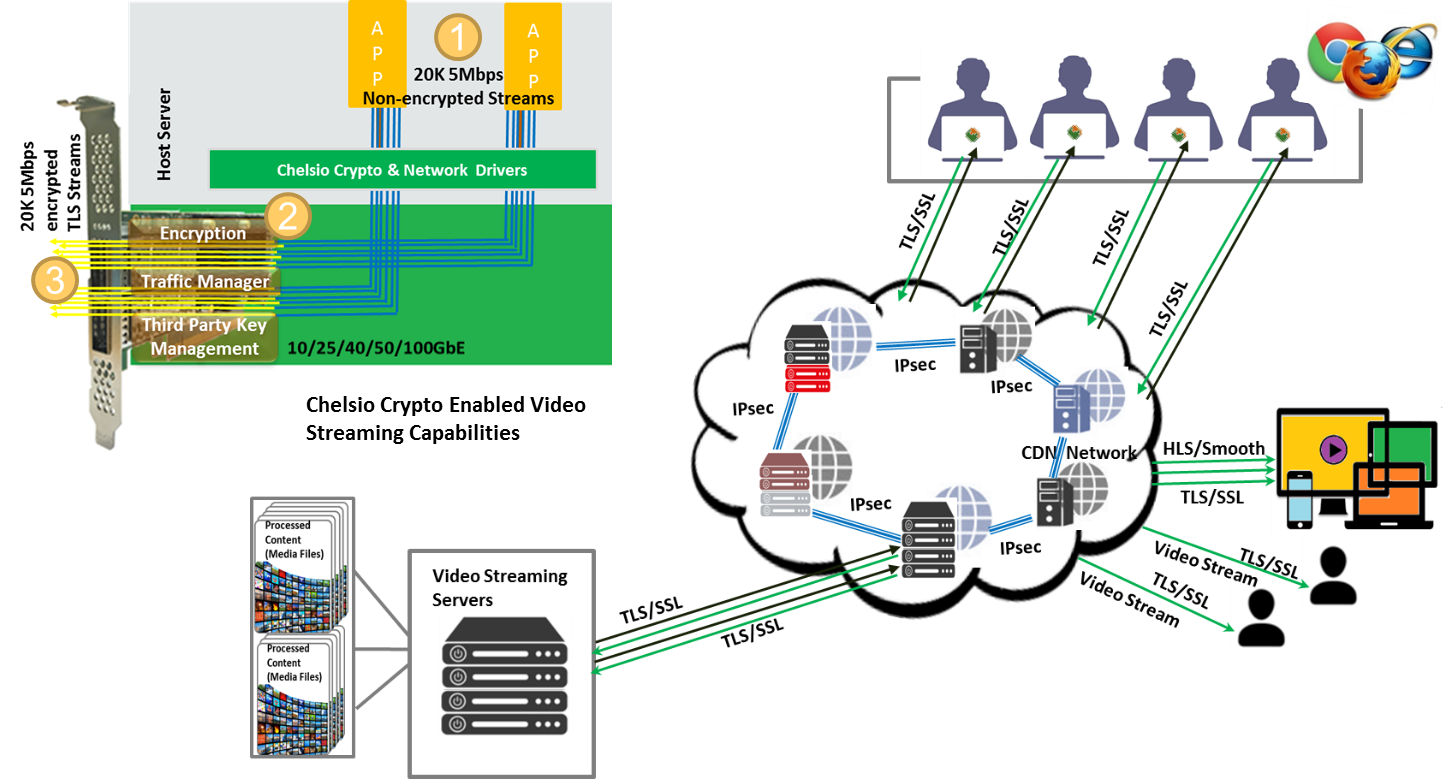
Reference Use CasesInline Encryption for Media Streaming – CDN Secure CloudContent delivery networks (CDNs) are globally distributed network of Point of Presence (POP) or proxy servers deployed in multiple datacenters. The goal of these large, broad-distribution of CDNs is to serve content, including on-demand/live streaming media, web servers providing downloadable media files to end-users over HTTP with high availability and high performance.
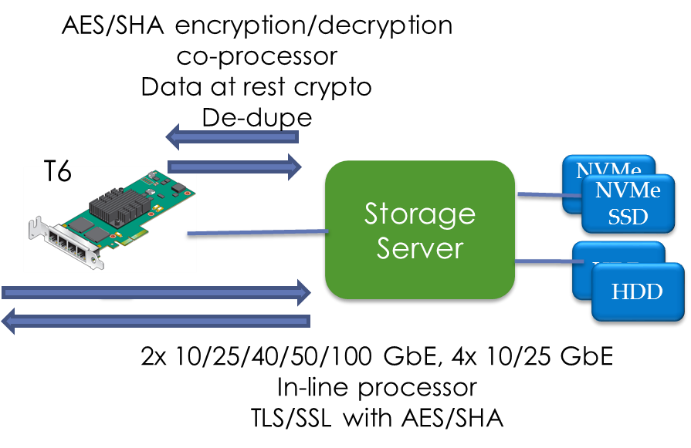
In the above figure (Chelsio Crypto Enabled Video Streaming Capabilities), a CDN server (1) delivers 20K 5Mpbs streams of content (video, movie, IPTV, etc.) using a single T6 adapter. It offloads 20K TLS/SSL connections (3) and each of these connections is traffic-managed by the integrated traffic manager (2) to proceed at 5Mbps rate with low jitter. This combined with other capabilities like TCP/UDP Segmentation Offload, Pacing, TCP Traffic Management and Traffic classification/filtering provides much needed acceleration for the on-demand/live streaming media edge servers. The inbuilt T6 traffic manager is capable of supporting up to 16 traffic classes concurrently. For example, there can be a 25Mbps group in addition to the 5Mbps group. Data-at-Rest encryption/decryptionThe T6 Data at-rest encryption/decryption uses the T6 crypto Co-processor mode of operation, as shown in the following diagram. The cleartext to be encrypted, e.g., with AES-XTS algorithm, is sent to the T6 crypto engine and the ciphertext is returned. The decryption proceeds by sending the ciphertext, and the cleartext is returned. If encrypted data arrives on inbound T6 port, it is decrypted and/or authenticated and delivered to storage server stack:
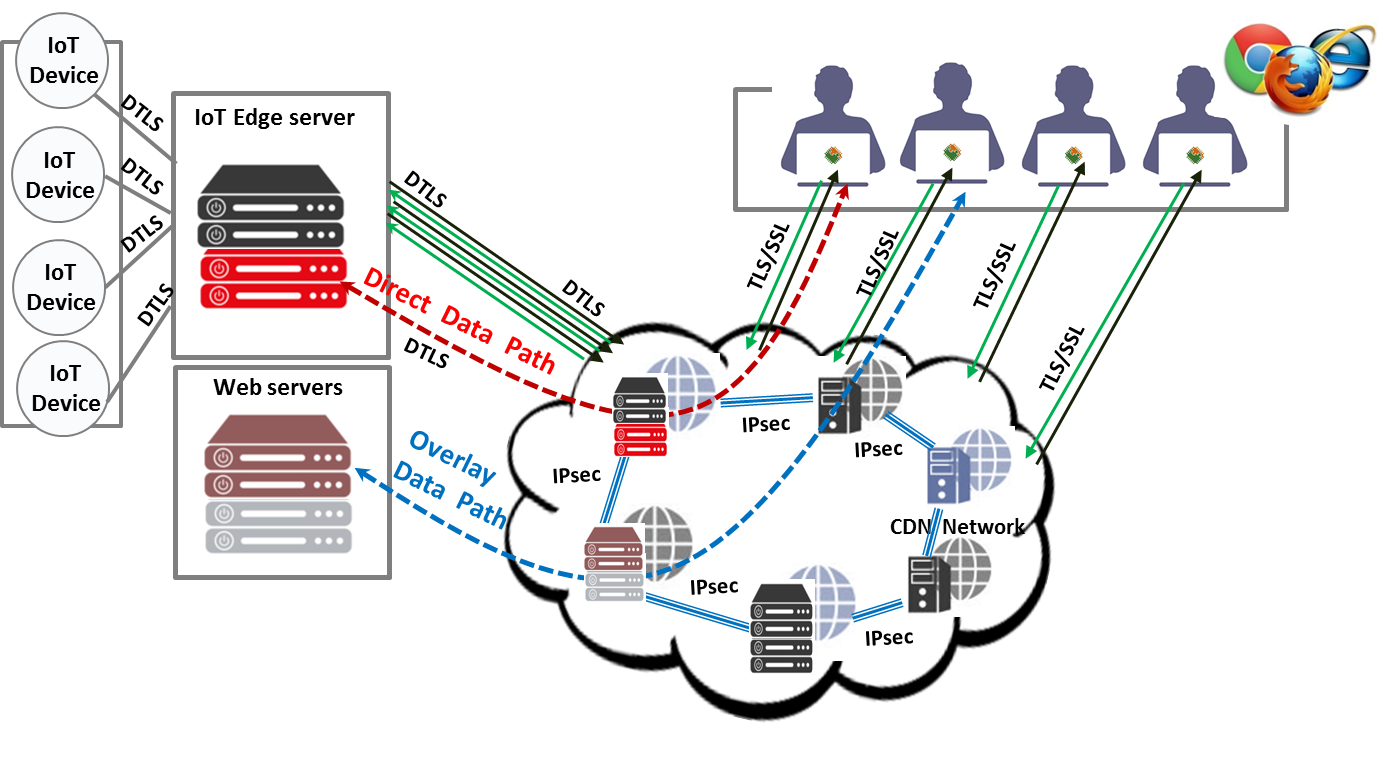
Data de-duplication fingerprintThe T6 crypto Co-processor can also be used for de-duplication fingerprint generation. For example, when offloaded iSCSI or NVMe-oF data is received, a fingerprint of the data is computed by injecting the data into the T6 crypto Co-processor and generating a SHA hash for the storage blocks, spreadsheets or PDF documents contained in the received data. The computed fingerprint can then be used to identify opportunities for de-duplication in the storing of the data. Secure Cloud: Inline Encryption for Web servers, IoT Devices and Overlay NetworksSecurity threats for web server clusters (normally located at the edge of the networks), cloud connected IoT devices (security camera, printers, medical devices) and autonomous vehicles are growing at a very fast pace. Chelsio’s 1/10/25/40/50/100GbE cryptographic offload and acceleration solution has integrated capabilities to enable point-to-point encryption (P2PE) network to secure both ends of the network.
As shown in the diagram above, IoT devices connected to an Edge server can be configured either to have an encrypted overlay network tunnel or provide an encrypted Direct Data Path access over the browser. Enabling security at the host level and capabilities to manage the network traffic at per flow basis provides a stringent security solution for today’s datacenter networks. |
Resources
- Accelerated Inline IPsec Communication with T6 25G (White Paper)
- Concurrent 100G Offload & Encryption on Arm (White Paper)
- Concurrent Offload & Encryption at 100GbE (White Paper)
- Apache TLS/SSL Acceleration at 100GbE (White Paper)
- Accelerated IPsec-VPN Communication with T6 (White Paper)
- Disk Encryption with 100GbE Crypto Accelerator (White Paper)
- Chelsio Terminator 6 (T6) In-line Acceleration of ubiquitous TLS/SSL delivers ground-breaking low latency, 100 Gigabit-Per-Second line-rate performance (Press Release)
- T6 100GbE Crypto Offload Performance (White Paper)
- Chelsio Terminator 6 ASIC 100GE Crypto Offload (White Paper)